Some people collect Windows utilities like windshields collect bugs. But for most of us, the word “utility” is key. If we find ourselves not using the tool a few times a week, we give it the heave-ho.
Utilities change all the time — and not always for the better. Newcomers usurp entrenched old favorites. Some find themselves in the news for the wrong reasons. So you have to refresh your set of tools time and again.
Here are 15 utilities that belong in every Windows user’s bag of tricks. They’re all free for personal use, and many are free for corporate use as well.
 1. Free Windows tool No. 1: SpiderOak: At least a dozen different products will sync files across multiple computers, tablets, and phones. SpiderOak stands out for its “zero knowledge” approach to security. In short, there’s no way the folks at SpiderOak can look at your data; you, alone, hold the encryption key. SpiderOak offers several unique features, including automatic file versioning, with recoverable history. It allows you to set up restricted Share Rooms where only invited people can participate. Dropbox is a popular and powerful alternative, but not without its security concerns. Box and SugarSync are also worth a look, but if security’s your No. 1 concern, SpiderOak is the product to consider.
1. Free Windows tool No. 1: SpiderOak: At least a dozen different products will sync files across multiple computers, tablets, and phones. SpiderOak stands out for its “zero knowledge” approach to security. In short, there’s no way the folks at SpiderOak can look at your data; you, alone, hold the encryption key. SpiderOak offers several unique features, including automatic file versioning, with recoverable history. It allows you to set up restricted Share Rooms where only invited people can participate. Dropbox is a popular and powerful alternative, but not without its security concerns. Box and SugarSync are also worth a look, but if security’s your No. 1 concern, SpiderOak is the product to consider.
2. Free Windows tool No. 2: SyncToy: Microsoft’s free SyncToy originated with the Windows XP PowerToy package and has been improved regularly. The latest version takes advantage of Sync Framework. To use SyncToy, pick two folders. Let’s call one Left (for reasons manifest in the screenshot) and the other Right. Here’s what you can do:
Synchronize: New files, and files changed since last sync, are copied between Left and Right folders. If a file has been renamed or deleted in one, it’s renamed or deleted in the other.
Echo: New and changed files are copied left to right, with renamed/deleted files on the left renamed/deleted on the right.
Contribute: Same as Echo, but deletions on the left are not deleted on the right.
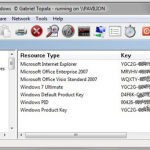 3. Free Windows tool No. 3: System Information for Windows: Over the years I’ve used many programs to retrieve software license keys, identify hardware, measure temperatures and fan speeds, run down memory chip details, and monitor CPU and network loads. Now, finally, I’ve found one program that does it all: System Information for Windows. This tool reports three separate types of data: (1) software, including file associations, ActiveX controls, and file name associations; (2) hardware, such as BIOS version, video and sound adapters, CPU details; (3) network, including neighborhood devices, shares, and open ports. There are hundreds of individual entries, all neatly arranged with a tree on the left of the screen.
3. Free Windows tool No. 3: System Information for Windows: Over the years I’ve used many programs to retrieve software license keys, identify hardware, measure temperatures and fan speeds, run down memory chip details, and monitor CPU and network loads. Now, finally, I’ve found one program that does it all: System Information for Windows. This tool reports three separate types of data: (1) software, including file associations, ActiveX controls, and file name associations; (2) hardware, such as BIOS version, video and sound adapters, CPU details; (3) network, including neighborhood devices, shares, and open ports. There are hundreds of individual entries, all neatly arranged with a tree on the left of the screen.
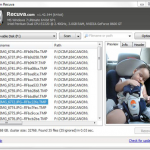 4. Free Windows tool No. 4: Recuva: File undelete has been a mainstay PC utility since DOS. But there’s never been an undeleter better than Recuva (pronounced “recover”): fast, thorough, and free. When you throw out the Windows Recycle Bin trash, the files aren’t destroyed; rather, the space they occupy is earmarked for new data. Undelete routines scan the flotsam and jetsam and put the pieces back together. As long as you haven’t added new data to a drive, undelete (almost) always works; if you’ve added some data, there’s still a good chance you can get most of the deleted stuff back. Recuva can also be used to undelete data on a USB drive, an SD card (see screenshot), and even an MP3 player.
4. Free Windows tool No. 4: Recuva: File undelete has been a mainstay PC utility since DOS. But there’s never been an undeleter better than Recuva (pronounced “recover”): fast, thorough, and free. When you throw out the Windows Recycle Bin trash, the files aren’t destroyed; rather, the space they occupy is earmarked for new data. Undelete routines scan the flotsam and jetsam and put the pieces back together. As long as you haven’t added new data to a drive, undelete (almost) always works; if you’ve added some data, there’s still a good chance you can get most of the deleted stuff back. Recuva can also be used to undelete data on a USB drive, an SD card (see screenshot), and even an MP3 player.
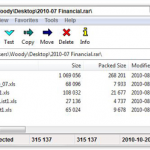 5. Free Windows tool No. 5: 7Zip:File archiver 7-Zip is a must-have even though Windows supports the zip format natively. Why? When Apple people send you RAR files, 7-Zip is the fast, easy, free way to handle them. 7-Zip also creates self-extracting EXE files, which can come in handy. And it supports AES-256 bit encryption. The interface rates as clunky by modern standards (see screenshot), but it gets the job done with zip, RAR, CAB, ARJ, TAR, 7z, and many lesser-known formats. It even lets you extract files from ISO CD images. A poster boy for open source, 7-Zip goes in easily, never nags, and wouldn’t dream of dropping an unwanted toolbar on your system — enlightened.
5. Free Windows tool No. 5: 7Zip:File archiver 7-Zip is a must-have even though Windows supports the zip format natively. Why? When Apple people send you RAR files, 7-Zip is the fast, easy, free way to handle them. 7-Zip also creates self-extracting EXE files, which can come in handy. And it supports AES-256 bit encryption. The interface rates as clunky by modern standards (see screenshot), but it gets the job done with zip, RAR, CAB, ARJ, TAR, 7z, and many lesser-known formats. It even lets you extract files from ISO CD images. A poster boy for open source, 7-Zip goes in easily, never nags, and wouldn’t dream of dropping an unwanted toolbar on your system — enlightened.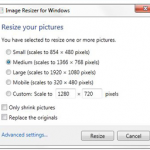 6. Free Windows tool No. 6: Image Resizer for Windows: Once upon a time, the Windows XP PowerToys project included a fabulous, simple, fast image resizer. Right-click on a photo fresh out of your camera, choose Resize Pictures, and the photo’s reduced in size to a fraction of the original. But XP came and went, and Microsoft didn’t keep the PowerToys updated. Enter Brice Lambson, a Microsoft employee with a heart of gold — and a mission to bring the free Image Resizer PowerToy to the latest versions of Windows. The updated PowerToy installs in seconds and works without a hitch. Microsoft still doesn’t support Image Resizer. But you can submit tech support questions on the download site, and they’re likely to be answered by Brice himself.
6. Free Windows tool No. 6: Image Resizer for Windows: Once upon a time, the Windows XP PowerToys project included a fabulous, simple, fast image resizer. Right-click on a photo fresh out of your camera, choose Resize Pictures, and the photo’s reduced in size to a fraction of the original. But XP came and went, and Microsoft didn’t keep the PowerToys updated. Enter Brice Lambson, a Microsoft employee with a heart of gold — and a mission to bring the free Image Resizer PowerToy to the latest versions of Windows. The updated PowerToy installs in seconds and works without a hitch. Microsoft still doesn’t support Image Resizer. But you can submit tech support questions on the download site, and they’re likely to be answered by Brice himself.
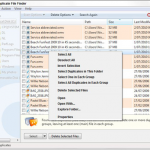 7. Free Windows tool No. 7: Auslogic Duplicate File Finder:If you’re a card-carrying member of the Ready, Shoot, Aim school of hard disk maintenance, pass this one by. But if you’re willing to carefully consider the information presented, Auslogic’s free Duplicate File Finder can help you reclaim enormous amounts of disk space. The trick with any duplicate file cleaner lies in judicious use of the gray matter between your ears. That said, Auslogic’s easy-to-use interface makes it relatively simple to find and select the files you want to delete, then stick the selected files in the Recycle Bin, where you can bring them back if need be.
7. Free Windows tool No. 7: Auslogic Duplicate File Finder:If you’re a card-carrying member of the Ready, Shoot, Aim school of hard disk maintenance, pass this one by. But if you’re willing to carefully consider the information presented, Auslogic’s free Duplicate File Finder can help you reclaim enormous amounts of disk space. The trick with any duplicate file cleaner lies in judicious use of the gray matter between your ears. That said, Auslogic’s easy-to-use interface makes it relatively simple to find and select the files you want to delete, then stick the selected files in the Recycle Bin, where you can bring them back if need be.
8. Free Windows tool No. 8: Revo Uninstaller Freeware: Revo Uninstaller truly uninstalls programs and does so in an unexpected way. When you use Revo, it runs the program’s uninstaller and watches while the uninstaller works, looking for the location of program files and for Registry keys that the uninstaller zaps. It then goes in and removes leftover pieces, based on the locations and keys that the program’s uninstaller took out. Revo also consults its own internal database for commonly left-behind bits, then roots those out. Revo gives you a great deal of flexibility in deciding just how much you want to clean. The not-free Pro version monitors your system when you install a program, making removal easier and more complete.
 It’s hard to pick among the high-quality, free image editors. IrfanView has tremendous viewing, organizing, and resizing capabilities. GIMP ships with powerful tools and an enormous array of add-ins. FastStone lets you edit full-screen and allows screen captures. That doesn’t even brush the surface of the Picasa vs. Windows Live Photo Gallery maelstrom — a religious debate worthy of volumes. For powerful, simple-to-use photo editing, with layers, plug-ins, and all sorts of special effects, along with a compact, easily understood interface, I’ll stick with Paint.Net. Although it requires the .Net Framework, the program puts all the editing tools a nonprofessional might expect into an intuitive package.
It’s hard to pick among the high-quality, free image editors. IrfanView has tremendous viewing, organizing, and resizing capabilities. GIMP ships with powerful tools and an enormous array of add-ins. FastStone lets you edit full-screen and allows screen captures. That doesn’t even brush the surface of the Picasa vs. Windows Live Photo Gallery maelstrom — a religious debate worthy of volumes. For powerful, simple-to-use photo editing, with layers, plug-ins, and all sorts of special effects, along with a compact, easily understood interface, I’ll stick with Paint.Net. Although it requires the .Net Framework, the program puts all the editing tools a nonprofessional might expect into an intuitive package.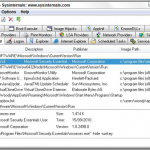 10. Free Windows tool No. 10: Autoruns: Programs that run automatically when Windows starts bedevil everyone. This industrial-strength autostart listing tool knows all and lets you do something about it. If you’ve never used Autoruns, you’re in for a shock. Autostarting programs lurk in the most obscure corners of Windows. The Everything tab (shown in the screenshot) lists every program that starts automatically, in the order in which it is run. Click on the program to see details. Right-click and choose Search Online to look up the program on the Web, using your default browser and search engine. You can filter out the Microsoft programs, and have Autoruns show just the third-party interlopers deposited on your machine.
10. Free Windows tool No. 10: Autoruns: Programs that run automatically when Windows starts bedevil everyone. This industrial-strength autostart listing tool knows all and lets you do something about it. If you’ve never used Autoruns, you’re in for a shock. Autostarting programs lurk in the most obscure corners of Windows. The Everything tab (shown in the screenshot) lists every program that starts automatically, in the order in which it is run. Click on the program to see details. Right-click and choose Search Online to look up the program on the Web, using your default browser and search engine. You can filter out the Microsoft programs, and have Autoruns show just the third-party interlopers deposited on your machine.
11. Free Windows tool No. 11: LastPass: Store all your passwords on a website. Sounds crazy, right? I’d been using AI Roboform to manage passwords for years, until I bumped into this cloud password manager. Like Roboform, LastPass keeps track of your user IDs, passwords, and other settings, then offers them to you with a click. But there’s a big difference. Roboform stores your passwords on your PC. LastPass encrypts them, then stores them in the cloud. LastPass does its AES-256 encrypting and decrypting on your PC, using a master password that you have to provide — and remember. The data stored in the cloud is encrypted, and without the key, the stored passwords can’t be broken, unless you can crack AES-256 encryption.
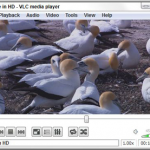 12. Free Windows tool No. 12: VLC Media Player:Another poster child for open source, VLC Media Player plays just about anything — including YouTube Flash FLV files — with no additional software, downloads, or headaches. Unlike other media players (notably the versatile but complex KMPlayer), VLC sports simple, Spartan controls; built-in codecs for almost every file type imaginable; and a large, vocal online support community. VLC plays Internet streaming media with a click, records played media, converts between file types, and even supports individual-frame screenshots. VLC is well-known for tolerating incomplete or damaged media files. It will even start to play downloaded media before the download’s finished.
12. Free Windows tool No. 12: VLC Media Player:Another poster child for open source, VLC Media Player plays just about anything — including YouTube Flash FLV files — with no additional software, downloads, or headaches. Unlike other media players (notably the versatile but complex KMPlayer), VLC sports simple, Spartan controls; built-in codecs for almost every file type imaginable; and a large, vocal online support community. VLC plays Internet streaming media with a click, records played media, converts between file types, and even supports individual-frame screenshots. VLC is well-known for tolerating incomplete or damaged media files. It will even start to play downloaded media before the download’s finished. 13. Free Windows tool No. 13: Jaangle:While VLC excels at playing videos, Jaangle covers the music bases, with the best combination of tagging and library support I’ve seen. Jaangle reaches out to the Net and retrieves a huge array of ancillary information about the music. If you’re tired of seeing the same old album covers, it’s like a breath of fresh air. The tag editor’s just a right-click away. More than that, you can right-click on a song and download the Google Lyrics, right inside Jaangle. Finally, we’re seeing online music libraries used for something other than ordering more songs. With customizable options to slice and dice, reorder and reorganize, Jaangle takes a fresh approach to organizing and managing a music collection.
13. Free Windows tool No. 13: Jaangle:While VLC excels at playing videos, Jaangle covers the music bases, with the best combination of tagging and library support I’ve seen. Jaangle reaches out to the Net and retrieves a huge array of ancillary information about the music. If you’re tired of seeing the same old album covers, it’s like a breath of fresh air. The tag editor’s just a right-click away. More than that, you can right-click on a song and download the Google Lyrics, right inside Jaangle. Finally, we’re seeing online music libraries used for something other than ordering more songs. With customizable options to slice and dice, reorder and reorganize, Jaangle takes a fresh approach to organizing and managing a music collection.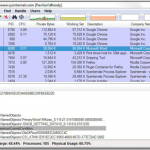 14. Free Windows tool No. 14: Process Explorer: The granddaddy of program monitors, Microsoft’s Process Explorer is up to Version 15. If you’ve never used this tool, you have no idea what’s going on under Windows’ covers. If you have, this version boasts new tricks and a much-needed makeover for the CPU and memory monitor. PE shows all running processes and subprocesses; with a click or mouseover, it divulges details about what’s really going on. Want to know which program has a file locked? Curious about the origin of those svchost.exe programs running on your machine? PE also tells you everything about CPU cycles, memory usage, and I/O. Best of all, PE doesn’t have an installer. It just runs — and runs well.
14. Free Windows tool No. 14: Process Explorer: The granddaddy of program monitors, Microsoft’s Process Explorer is up to Version 15. If you’ve never used this tool, you have no idea what’s going on under Windows’ covers. If you have, this version boasts new tricks and a much-needed makeover for the CPU and memory monitor. PE shows all running processes and subprocesses; with a click or mouseover, it divulges details about what’s really going on. Want to know which program has a file locked? Curious about the origin of those svchost.exe programs running on your machine? PE also tells you everything about CPU cycles, memory usage, and I/O. Best of all, PE doesn’t have an installer. It just runs — and runs well. 15. Free Windows tool No. 15: PicPick: If you’ve tried to capture fleeting images with the Windows 7 Snipping Tool, you’re in for a treat. PicPick lets you take screenshots with the key combination of your choice and doesn’t make ephemeral items on the screen run for cover. You can, depending on the key combo, capture a full screen, an active window, or a rectangular or freehand region on the screen. If you need to shoot against a single-color background, the PicPick Whiteboard lets you “erase” parts of the screen. The PicPick editor includes tools for resizing and editing, automatic file naming, and on-screen magnification. It includes a pixel ruler, a color picker, and a half-dozen other screenshooting aids.
15. Free Windows tool No. 15: PicPick: If you’ve tried to capture fleeting images with the Windows 7 Snipping Tool, you’re in for a treat. PicPick lets you take screenshots with the key combination of your choice and doesn’t make ephemeral items on the screen run for cover. You can, depending on the key combo, capture a full screen, an active window, or a rectangular or freehand region on the screen. If you need to shoot against a single-color background, the PicPick Whiteboard lets you “erase” parts of the screen. The PicPick editor includes tools for resizing and editing, automatic file naming, and on-screen magnification. It includes a pixel ruler, a color picker, and a half-dozen other screenshooting aids.
